Stuxnet was a game changer, used as a malicious cyber weapon believed to be a jointly built American-Israeli team, although no organization or state officially admitted responsibility.
Cyber attacks are no longer just stealing private emails and bank account numbers.
The most worrisome targets are called “Industrial Control Systems” which control EVERYTHING.

The Director of Homeland Security has expressed real concern our countries infrastructure could be vulnerable to a cyber attack and with it, our citizens.
The Washington Post claimed Stuxnet was developed to sabotage Iran’s nuclear program which would seem like a long series of unfortunate accidents..
Stuxnet specifically targeted Programmable Logic Controllers (PLCs), which allowed control centrifuges used for separating nuclear material, to spin faster than normal, causing the centrifuges to tear themselves apart.

Stuxnet’s design architecture was not domain-specific and could be tailored as a platform for attacking modern Supervisory Control and Data Acquisition (SCADA basically internal monitoring software ) and PLC’s (assembly lines or power plants etc).
Stuxnet has three modules:
- worm which executes all routines related to the main payload of the attack
- link file that automatically executes the propagated copies of the worm; basically what makes it spread)
- rootkit component responsible for hiding all malicious files and processes, preventing detection of the presence of Stuxnet.

The worm then propagates across the network, it scans for
- Siemens Step7 software
- computers controlling a PLC.
In the absence of either of those Stuxnet, becomes dormant inside the computer.

If both are there, Stuxnet introduces the infected rootkit onto the PLC and Step7 software and works by:
- modifying the codes
- giving unexpected commands to the PLC
- returning a loop of normal operations values feedback to the users
In 2015, Kaspersky Labs‘based in Rusia found another highly sophisticated espionage platform created by an “Equation Group”

The group had used two of the same zero-day attacks before they were used in Stuxnet, and their use in both programs were similar.

Researchers reported
“the similar usage of both exploits together in different computer worms,around the same time, indicates that the Equation Group and the Stuxnet developers are either the same or working closely together”.
The director of Kaspersky Lab’s global research and analysis team, believes the Equation Group cooperates with the Stuxnet and Flame groups from a position of clear superiority.

The worm initially spreads indiscriminately, but includes a highly specialized malware payload designed to target only Siemens (SCADA) systems, which are configured to control and monitor specific industrial processes.
Stuxnet infects by subverting the Step-7 software application used to reprogram these devices.
Different variants of Stuxnet targeted 5 Iranian organizations.
The probable target: uranium enrichment infrastructure in Iran
Symantec noted in August 2010 that 60% of the infected computers worldwide were in Iran .

If the suspected Stuxnet creators at the US National Security Agency wanted to wipe out Iran’s entire working fleet of centrifuges, they could have done so with Ninja Stuxnet.
But Natanz had a standing fleet of centrifuges ready to go whenever the operating ones failed.
Engineers could have also ripped out busted gear and got things back up quickly, mitigating much of the 2 yr set back, the Stuxnets were said to have inflicted.

Stuxnet 0.5 was stealthy, which meant the centrifuges simply continued to fail every month at a high but not overzealous rate.
It made Natanz operators look incompetent.
Kaspersky says, it required the resources of a nation-state.

It required testing on an epic scale carried out on a working uranium enrichment test bed composed of Natanz’s unique patchwork of systems.
International Atomic Energy Agency inspectors and Iranian technicians left Natanz

But civilian infrastructure is a much softer target, for example:
Sydney’s energy plants, Melbourne’s transport network and runs on standard equipment which a smaller group could purchase, to test their own malware weapons.
This is a bigger risk than attackers breaking into industrial control systems via the internet which has largely yet to be realized.

Imagine a virus that shuts down the electricity in your neighborhood, turns every traffic light green, or even causes the gas pressure in a pipeline to build up to explosive levels.
Standard equipment means intelligence gathering is much easier.
An engineer in a Sydney’s power plant: for example may be familiar with infrastructure in place in other energy facilities, meaning , unlike the ultra-customized Stuxnets, they could use the same familiarity against multiple targets.

The cost of such attacks would be much less than the investment in the Natanz malware weapons.
It is estimated “well over” half the cost of Stuxnet’s development, was due to their bid to hide the attack.
“Stuxnet–inspired attackers will not necessarily place the same emphasis on disguise; they may want the victim to know that they are under cyber attack, and perhaps even publicly claim credit for it.”

Chris Matyszczyk from CNET reported how the Atomic Energy Organization of Iran e-mailed F-Secure‘s chief research officer to report a new instance of malware.
December 2012, an Iranian semi-official news agency announced there was a cyber attack by Stuxnet, this time on a power plant and some industries in south Iran.

According to expert Eugene Kaspersky, the worm also infected a nuclear power plant in Russia.
Noted, however, that since the power plant was not connected to the public internet, the system should remain safe

The reason for the discovery this time, was caused by the virus accidentally spreading beyond its intended target (the Natanz plant) due to a programming error introduced in an update; this led to the worm spreading to an engineer’s computer connected to the centrifuges, and spreading further when the engineer returned home and connected his computer to the internet.
Kaspersky Lab is a Russian multinational cyber security and anti-virus provider headquartered in Moscow which develops and sell antivirus, internet security, password management, endpoint security, and other cyber security products and services.
Kaspersky ranks 4th in the global ranking of antivirus vendors by revenue, first estimated that Stuxnet started spreading around March or April 2010, but the first variant of the worm appeared in June 2009.
By July 2010, its existence became widely known, a distributed denial-of-service attack (DOS) was made on the servers for two leading mailing lists on industrial-systems security.
This attack, was from an unknown source but likely related to Stuxnet.
It disabled one of the lists and thereby interrupted an important source of information for power plants and factories.
In a different theory, researchers at Symantec point to an uncovered version of Stuxnet which was used to attack Iran’s nuclear program in 2007, being developed as early as 2005, when Iran was still setting up its uranium enrichment facility.
The second variant, appeared with substantial improvements, in 2010, apparently because its authors believed that Stuxnet was not spreading fast enough; also a third, with minor improvements, appeared which contains a component with a built time-stamp.

In the UK, Sky News reported it had received information from an anonymous source at an unidentified IT security organization that Stuxnet, or a variation of it, had been traded on the black market.
Within a year, the virus had spread to every continent, including the computer systems of major U.S. companies and government branches.
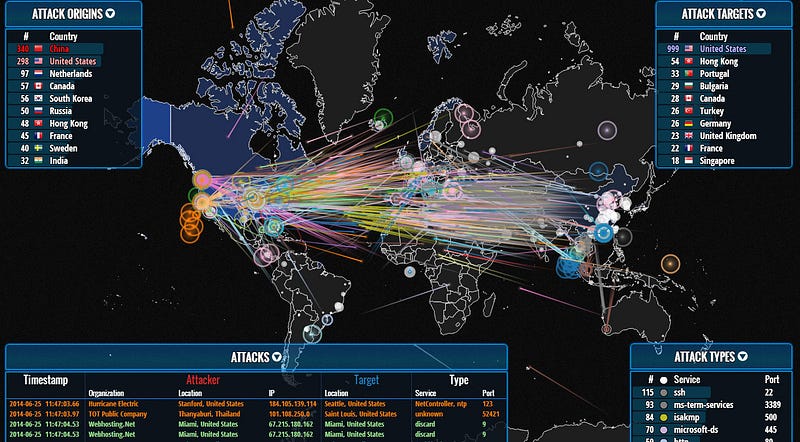
Included in these breaches were many “Industrial Control Systems.”
The cyber security company that came to the rescue was Symantec Research Labs of Santa Monica, California.
Piecing together a few keywords from the code, they coined the virus “STUXNET.”
They didn’t know it yet, what they had stumbled across was an advanced form of the virus which wreaked havoc on the Iranian Natanz Nuclear Plant.
Even the Department of Homeland Security was in the dark, as they tried to asses if the worm was a threat.
STUXNET was something new.

It was enormously complex, had almost no errors, and capable of seamlessly spreading to connected devices without any need for user interface (this was done by using “zero-day exploits” and classified the virus as a “worm”).
Symantec studied the spread of Stuxnet and showed the main affected countries in the early days were Iran, Indonesia and India:
Country Share of infected computers
Iran 58.85%
Indonesia 18.22%
India 8.31%
Azerbaijan 2.57%
United States 1.56%
Pakistan 1.28%
Other countries 9.2%
Iran was reported to have “beefed up” its cyber warfare capabilities following the Stuxnet attack, and has been suspected of retaliatory attacks against US banks.
Unlike most malware, Stuxnet does little harm to computers and networks which do not meet specific configuration requirements,
“The attackers took great care to make sure only their designated targets were hit…
It was a marksman’s job.”
While the worm is promiscuous, it makes itself inert if Siemens software is not found, contains safeguards to prevent an infected computer from spreading the worm to more than three others, and erase itself.
Stuxnet targets contain, among other things, a code for a man-in-the-middle attack which fakes industrial process control sensor signals, so an infected system does not shut down due to detected abnormal behavior.
Such complexity is very unusual for malware.
Initially spreading the use of infected, removable drives such as USB flash , and other exploits, such as peer-to-peer RPC to infect and update other computers inside private networks not directly connected to the internet.

The number of zero-day exploits used is unusual, as they are highly valued and malware creators do not typically make use of (and simultaneously make visible) four different zero-day exploits in the same worm.
Among these exploits, were remote code execution on a computer with printer sharing enabled, and the LNK/PIF vulnerability, in which file execution is accomplished, when an icon is viewed in Windows Explorer; negating the need for user interaction.
Stuxnet is unusually large, half a megabyte in size, and written in several different programming languages (including C and C++) which is also irregular for malware.
The Windows component of the malware spreads relatively quickly and indiscriminately.
Two websites in Denmark and Malaysia were configured as command and control servers for the malware, allowing it to be updated, and for industrial espionage conducted by uploading information.
Both of these websites have subsequently been taken down as part of a global effort to disable malware.


The layers include policies and procedures, awareness and training, network segmentation, access control measures, physical security measures, system hardening, e.g., patch management, system monitoring, anti-virus and intrusion prevention system (IPS).
The standards and best practice with improper synthesis, is recommend as starting a risk analysis and a control system security assessment.

The cost of developing sophisticated malware like Stuxnet and Flame has dropped dramatically in recent years from $100 million to just $10,000 – dramatically lowering the barrier to entry to the global cyber-arms race.
Experts believe that Stuxnet required the largest and costliest development effort in malware history.
Developing its many capabilities would have required a team of highly capable programmers, in-depth knowledge of industrial processes, and an interest in attacking industrial infrastructure.
Eric Byres, who has years of experience troubleshooting Siemens systems, told Wired that writing the code would have taken many man-months, if not years.
Symantec estimates that the group developing Stuxnet would have consisted of anywhere from 5 to 30 people, and would have taken six months to prepare.
The Guardian, the BBC and The New York Times all claimed that (unnamed) experts studying Stuxnet believe the complexity of the code indicates that only a nation-state would have the capabilities to produce it.

The self-destruct and other safeguards within the code could imply that a Western government was responsible, or at least is responsible in the development of it.
Ralph Langner, the researcher who identified Stuxnet, first speculated in Sept 2010 that the malware was of Israeli origin, and that it targeted Iranian nuclear facilities.
However statedin a TED Talk in Feb 2011,
“My opinion is that the Mossad is involved, but the leading force is not Israel.
The leading force behind Stuxnet is the cyber superpower – there is only one; and that’s the United States.”
Kevin Hogan, Senior Director of Security Response at Symantec, reported that the majority of infected systems were in Iran (about 60%),which has led to speculation that it may have been deliberately targeting “high-value infrastructure” in Iran including either the Bushehr Nuclear Power Plant or the Natanz nuclear facility.
According to the Israeli newspaper Haaretz, in 2010 experts on Iran and computer security specialists were increasingly convinced Stuxnet was meant “to sabotage the uranium enrichment facility at Natanz – where the centrifuge operational capacity had dropped by 30 percent.
“On 23 November 2010 it was announced that uranium enrichment at Natanz had ceased several times because of a series of major technical problems.
A “serious nuclear accident” (supposedly the shutdown of some of its centrifuges) occurred at the site in the first half of 2009, which is speculated to have forced the head of Iran’s Atomic Energy Organization to resign.
Statistics published by the Federation of American Scientists (FAS) show that the number of enrichment centrifuges operational in Iran mysteriously declined from about 4,700 to about 3,900 beginning around the time the nuclear incident WikiLeaks mentioned would have occurred.
The Institute for Science and International Security (ISIS) suggests Stuxnet is a reasonable explanation for the apparent damage at Natanz, and may have destroyed up to 1000 centrifuges (10 percent) sometime between November 2009 – late January 2010. The authors conclude:
The worm worked by infecting Iranian IR-1 centrifuge. 27 days later, the worm went back into action, slowing the infected centrifuges down to a few hundred hertz for a full 50 minutes.

Stresses from the excessive, then slower, speeds caused the aluminum centrifugal tubes to expand, often forcing parts of the centrifuges into sufficient contact with each other, to destroy the machine.
IAEA cameras installed in the Natanz facility, recorded sudden dismantling and removal of approximately 900–1000 centrifuges, during the time the Stuxnet worm was reportedly active .
Iranian technicians, however, were able to quickly replace the centrifuges and the report concluded, uranium enrichment was likely, only briefly disrupted.
February 2011, ISIS released a report concluding:
Assuming Iran exercises caution, Stuxnet is unlikely to destroy more centrifuges at the Natanz site.
The ISIS report notes, Iranian authorities have attempted to conceal the breakdown by installing new centrifuges on a large scale plant.
Iran likely cleaned the malware from its control systems.
Nonetheless, there remain important questions about why Stuxnet destroyed only 1,000 centrifuges.
One observation is, it may be harder to destroy centrifuges by use of cyber attacks, than often believed.
The Associated Press reported the semi-official Iranian Students News Agency released a statement stating, experts from the Atomic Energy Organization of Iran met the previous week to discuss, how Stuxnet could be removed from their systems.
The Director of Information Technology Council at the Iranian Ministry of Industries and Mines, has said,
“An electronic war has been launched against Iran… This computer worm is designed to transfer data about production lines from our industrial plants to locations outside Iran.”

In response to the infection, Iran has assembled a team to combat it.
With more than 30,000 IP addresses affected in Iran, an official said the infection is fast spreading and the problem has been compounded by the ability of Stuxnet to mutate.
Iran has set up its own systems to clean up infections and has advised against using the Siemens SCADA antivirus, since it is suspected the antivirus is actually embedded with codes, which update Stuxnet instead of eradicating it.

According to Hamid Alipour, deputy head of Iran’s government information technology company,
“The attack is still ongoing and new versions of this virus are spreading.
” He reports his company had begun the cleanup process at Iran’s “sensitive centers and organizations.”
“We had anticipated that we could root out the virus within one to two months, but the virus is not stable, and since we started the cleanup process – 3 new versions of it have been spreading”, he told the Islamic Republic News Agency .

On 29 November 2010, Iranian president Mahmoud Ahmadinejad, stated for the first time, a computer virus caused problems with the controller which handled centrifuges at Natanz facilities.
According to Reuters, he told reporters
“They succeeded in creating problems for a limited number our centrifuges with the software, they installed”.

On the same day two Iranian nuclear scientists were targeted separately, but nearly simultaneous car bomb attacks, near Shahid Beheshti University in Tehran.
Majid Shahriari, a quantum physicist was killed.
Fereydoon Abbasi, a high-ranking official at the Ministry of Defense, was seriously wounded.
Wired speculated that the assassinations could indicate, whoever was behind Stuxnet felt it was not sufficient to stop the nuclear program.
January 2010, another Iranian nuclear scientist, a physics professor at Tehran University, had been killed in a similar bomb explosion.
On 11 January 2012, a Director Natanz’s nuclear enrichment facility, Mostafa Ahmadi Roshan, was killed in an attack quite similar to the one that killed Shahriari.

European and US officials, along with private experts, said Iranian engineers were successful in neutralizing and purging Stuxnet from their country’s nuclear machinery.
Given the growth in Iranian enrichment capability, in 2010, the country may have intentionally put out misinformation to cause Stuxnet‘s creators to believe, the worm was more successful in disabling the Iranian nuclear program than it actually was.
Israel, through Unit 8200, has been speculated to be the country behind Stuxnet,in many media reports and experts such as Richard A. Falkenrath, former Senior Director for Policy and Plans within the US Office of Homeland Security.

Yossi Melman, who covers intelligence for the Israeli daily newspaper Haaretz ,and wrote a book about Israeli intelligence, also suspected that Israel was involved, noting that Meir Dagan, the former head of the national intelligence agency Mossad, had his term extended in 2009 because he was said to be involved in important projects.
Israel has not publicly commented on the Stuxnet attack but confirmed cyber warfare is now among the pillars of its defense doctrine, with a military intelligence unit set up to pursue both defensive and offensive options.
In 2009, a year before Stuxnet was discovered, Scott Borg of the United States Cyber-Consequences Unit (US-CCU) suggested, Israel might prefer to mount a cyber-attack, rather than a military strike, on Iran’s nuclear facilities.
Borg stated, “Israel certainly has the ability to create Stuxnet and there is little downside to such an attack because it would be virtually impossible to prove who did it.
Iran uses P-1 centrifuges at Natanz, the design A. Q. Khan stole in 1976 and took to Pakistan.
His black market nuclear-proliferation network sold P-1s to Iran.

Experts believe Israel, also somehow acquired P-1s and tested Stuxnet on the centrifuges, installed at the Dimona facility, part of its own nuclear program.
Some equipment may be from the United States, which received P-1s from Libya’s former nuclear program.

Some have also referred to several clues in the code such as a concealed reference to the word “MYRTUS”, believed to refer to the Myrtle tree, or Hadassah in Hebrew.
Hadassah was the birth name of the former Jewish queen of Persia, Queen Esther.
However, it may be that the “MYRTUS” reference is simply a misinterpreted reference to SCADA components known as RTUs (Remote Terminal Units) and that this reference is actually “My RTUs”–a management feature of SCADA.

Such data is not conclusive, since, as written by Symantec,
“Attackers would have the natural desire to implicate another party” with a false flag.
A diplomatic cable obtained by WikiLeaks showed how the United States was advised to target Iran’s nuclear capabilities through ‘covert sabotage‘.

Sean McGurk, a former cyber security official at the Department of Homeland Security noted, the Stuxnet source code could now be downloaded online and modified to be directed at new target systems.
Speaking of the Stuxnet creators, he said,
“They opened the box.
They demonstrated the capability… It’s not something that can be put back.”
Langner speculated that the infection may have spread from USB drives, belonging to Russian contractors since, the Iranian targets were not accessible via the Internet.
Sandro Gaycken from the Free University Berlin, argued the attack on Iran was a ruse to distract from Stuxnet’s real purpose.
According to him, its broad dissemination in more than 100,000 industrial plants worldwide suggests a field test of a cyber weapon, in different security cultures, testing their preparedness, resilience, and reactions, all highly valuable information for a cyberwarfare unit
In 2013, Edward Snowden claimed that Stuxnet was cooperatively developed by the United States and Israel.

According to a report by Reuters, the NSA also tried to sabotage North Korea’s nuclear program using a version of Stuxnet.
The North Korean nuclear program shares many similarities with the Iranian, both having been developed with technology transferred by Pakistani nuclear scientist A.Q. Khan.
The effort failed, however, because North Korea’s extreme secrecy and isolation made it impossible to introduce Stuxnet into the nuclear facility.
In 2011, a new worm was found, thought to be related to Stuxnet.
The Laboratory of Cryptography and System Security (CrySyS) of Budapest University of Technology and Economics analyzed the malware, naming the threat Duqu.

Symantec continued the analysis, calling it “nearly identical to Stuxnet, but with a completely different purpose”.
The main component used in Duqu is designed to capture information such as keystrokes and system information.
The ex filtrated data may be used to enable a Stuxnet-like attack.
Kaspersky Lab’s director of global research and analysis spoke to Reuters about research results showing, the platform for Stuxnet and Duqu both originated in 2007, referred to as Tilde d,due to the ~d, at the beginning of the file names.
Also uncovered in this research, was the possibility for 3 more variants based on, Tilde d platform.
In2012, a new malware was found, researchers named the program “Flame” after one of its modules.
After analyzing the code of Flame, there is a strong relationship between it and Stuxnet.

Since 2010, there has been extensive international media coverage on Stuxnet and its aftermath.
Holger Stark called Stuxnet the “first digital weapon of geopolitical importance, it could change the way wars are fought.”
Ultimately, some claim the “extensive media coverage afforded to Stuxnet has only served as an advertisement for vulnerabilities used by various cyber criminal groups.”
While that may be the case, media coverage has also increased awareness of cyber security threats.

General James Cartwright, former head of the U.S. Strategic Command, leaked information related to Stuxnet.
The leak initial investigation which ensnared him was when “Confront and Conceal” an article in The Times described Operation Olympic Games
F.B.I. agents came to believe General Cartwright was a source for a 2012 Newsweek article discussing cyber attacks against Iran.
He pleaded guilty for lying to FBI agents pursuing an investigation into the leak.
However, President Obama pardoned Cartwright, saving him from possible prison time.

However, Obama took serious action against Russia, expelling 35 diplomats and issuing sanctions to Russian intelligence agencies.
The reason: Surfacing Russian breaches of US cybersecurity.
The Department of Homeland Security and the FBI released a report ,detailing Russian malware code—called “Grizzly Steppe”— used to hack emails within the Democratic National Committee, in the lead up to the 2016 election.
Now, US officials confirmed similar computer code was found on a company laptop from a utility company in Vermont, according to the Washington Post.

The presence of Russian malware, suggests other utilities may also have been targeted.
Electrical grids power homes, but more worryingly, critical infrastructure like hospitals and other emergency departments.
Such attacks have already happened in Ukraine.
Ukraine’s president Petro Poroshenko accused Russian intelligence of 6,500 cyberattacks in the past two months.
In December 2015, Russian malware disrupted power to 225,000 residents serviced by 3 separate electrical providers in Ukraine.